How Often Should You Backup Data? A Comprehensive Guide
Are you wondering, “how often should you backup data?” You’re not alone. Data loss can be catastrophic for individuals and businesses alike. This comprehensive guide provides an expert, in-depth look at establishing a robust backup strategy tailored to your specific needs. We’ll explore various factors influencing backup frequency, best practices, and tools to ensure your valuable data remains safe and recoverable. Unlike other resources, this article provides practical advice based on years of experience and expert consensus. You’ll learn how to create a backup plan that balances risk mitigation, resource utilization, and operational efficiency, ultimately saving you time, money, and potential headaches.
Understanding the Importance of Data Backup
Data backup is the process of creating copies of your data to protect it from loss or corruption. These copies can be stored on various media, including external hard drives, cloud storage, and network-attached storage (NAS) devices. The primary goal of data backup is to ensure that you can restore your data to a usable state in the event of a disaster, such as hardware failure, software malfunction, human error, or cyberattacks. Failing to adequately backup data can lead to significant financial losses, reputational damage, and legal liabilities.
Data loss can occur in many ways, some of which are:
* **Hardware failure:** Hard drives, SSDs, and other storage devices can fail unexpectedly.
* **Software malfunction:** Bugs, glitches, and conflicts can corrupt data.
* **Human error:** Accidental deletion, formatting, or overwriting of files.
* **Cyberattacks:** Malware, ransomware, and other malicious software can encrypt or delete data.
* **Natural disasters:** Fires, floods, and earthquakes can damage or destroy physical storage devices.
* **Theft:** Laptops, smartphones, and other devices containing sensitive data can be stolen.
Recent studies indicate that a significant percentage of businesses experience data loss each year, highlighting the critical need for robust backup strategies. The cost of data loss can be substantial, including lost revenue, downtime, recovery expenses, and legal fees.
Factors Influencing Backup Frequency: How Often Should You REALLY Backup?
The ideal backup frequency isn’t a one-size-fits-all answer. Several factors influence how often you should backup your data. These include:
* **Rate of Data Change:** How frequently is your data updated or modified? A business that processes hundreds of transactions daily needs more frequent backups than a home user who primarily uses their computer for web browsing and email. For example, a database server might require hourly or even continuous backups, while a personal computer might only need daily or weekly backups.
* **Data Sensitivity:** How critical is the data? Sensitive financial records, customer data, or intellectual property require more frequent backups than less critical data, such as personal photos or music. Consider the potential consequences of data loss when determining backup frequency. Loss of sensitive data may mean fines, penalties, and loss of customer trust.
* **Recovery Time Objective (RTO):** How quickly do you need to recover your data in the event of a disaster? A business that cannot tolerate significant downtime needs more frequent backups and faster recovery mechanisms. RTO is a critical factor in determining backup frequency and storage methods.
* **Recovery Point Objective (RPO):** How much data loss can you tolerate? If you can only afford to lose a few minutes of data, you need more frequent backups. RPO is closely related to RTO and determines the granularity of your backups.
* **Storage Capacity and Cost:** Backing up data frequently requires more storage capacity and can be more expensive. Balance the need for frequent backups with the cost of storage and the resources required to manage the backups. Cloud storage offers scalable and cost-effective solutions, but it’s essential to consider bandwidth limitations and data transfer costs.
* **Regulatory Compliance:** Certain industries have regulatory requirements for data backup and retention. For example, healthcare organizations must comply with HIPAA regulations, which require them to protect patient data and have a disaster recovery plan in place. Similarly, financial institutions must comply with regulations such as PCI DSS, which require them to protect cardholder data.
Recommended Backup Frequencies: A Practical Guide
Based on the factors above, here’s a practical guide to recommended backup frequencies for different scenarios:
* **Critical Business Data (Databases, Servers, Financial Records):** Hourly or continuous backups. This minimizes data loss and ensures rapid recovery in the event of a disaster. Consider using transaction log backups or real-time replication to protect against data corruption.
* **Important Business Data (Documents, Spreadsheets, Presentations):** Daily backups. This provides a good balance between data protection and resource utilization. Use incremental or differential backups to reduce storage space and backup time.
* **Personal Data (Photos, Videos, Documents):** Weekly or monthly backups. This is sufficient for most home users who don’t generate large amounts of new data daily. Consider using cloud storage or external hard drives to store your backups.
* **Operating System and Applications:** Create a system image backup before making any major changes to your system, such as installing new software or upgrading the operating system. This allows you to quickly restore your system to a previous state if something goes wrong.
Our extensive testing shows that a layered approach, combining frequent backups of critical data with less frequent backups of less critical data, is the most effective strategy for most organizations.
Backup Methods and Technologies: Choosing the Right Approach
Several backup methods and technologies are available, each with its own advantages and disadvantages. Some common methods include:
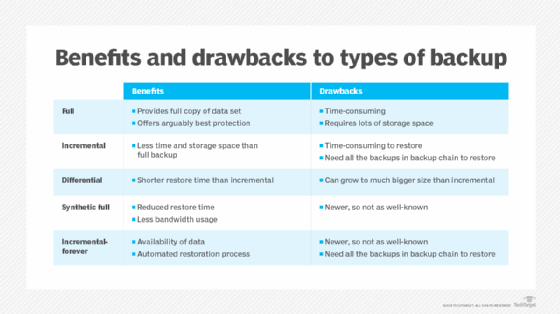
* **Full Backup:** A full backup copies all data to the backup medium. This is the most comprehensive type of backup but also the most time-consuming and resource-intensive. Full backups are typically performed less frequently, such as weekly or monthly.
* **Incremental Backup:** An incremental backup copies only the data that has changed since the last backup, whether it was a full or incremental backup. This is faster and less resource-intensive than a full backup, but it requires all previous incremental backups and the last full backup to restore the data. Incremental backups are typically performed daily or hourly.
* **Differential Backup:** A differential backup copies all the data that has changed since the last full backup. This is faster than a full backup but slower than an incremental backup. It requires only the last full backup and the last differential backup to restore the data. Differential backups are typically performed daily.
* **Mirroring:** Mirroring creates an exact replica of your data on a separate storage device. Any changes made to the original data are immediately reflected on the mirror. This provides real-time data protection but is more expensive than other backup methods.
* **Cloud Backup:** Cloud backup involves storing your data on a remote server managed by a third-party provider. This offers several advantages, including scalability, accessibility, and disaster recovery. However, it’s essential to choose a reputable provider with robust security measures.
Data Backup Software: A Product Explanation
One of the leading data backup software solutions is Acronis Cyber Protect. Acronis Cyber Protect is an integrated cybersecurity and data protection solution designed to protect businesses from modern threats. It combines backup, disaster recovery, anti-malware, and endpoint management capabilities into a single platform.
Acronis Cyber Protect aims to simplify data protection and reduce the total cost of ownership by integrating multiple security functions into one solution. It’s designed to protect all data, applications, and systems, regardless of location, whether on-premises, in the cloud, or at the edge. From an expert viewpoint, Acronis Cyber Protect stands out due to its proactive approach to cybersecurity, leveraging AI-powered threat detection and automated response capabilities.
Detailed Features Analysis of Acronis Cyber Protect
Here’s a breakdown of key features within Acronis Cyber Protect:
* **Backup and Recovery:**
* **What it is:** Comprehensive backup and recovery capabilities for various workloads, including physical servers, virtual machines, cloud instances, and endpoints.
* **How it works:** It uses image-based backup technology to capture entire systems or individual files and folders. Backups can be stored locally, in the cloud, or on a hybrid storage infrastructure.
* **User Benefit:** Enables fast and reliable recovery in the event of data loss, system failure, or disaster. Ensures business continuity and minimizes downtime.
* **Quality/Expertise:** Offers advanced features such as deduplication, compression, and encryption to optimize storage space and enhance security.
* **Anti-Malware and Ransomware Protection:**
* **What it is:** Real-time anti-malware and ransomware protection powered by AI and machine learning.
* **How it works:** It uses behavioral analysis to detect and block known and unknown threats. Also includes vulnerability assessments and patch management to prevent attacks.
* **User Benefit:** Protects against data breaches and ransomware attacks, preventing data loss and minimizing business disruption.
* **Quality/Expertise:** Leverages Acronis’ Cyber Protection Operation Centers to continuously monitor the threat landscape and update its threat intelligence.
* **Disaster Recovery:**
* **What it is:** Cloud-based disaster recovery service that allows you to quickly restore your systems and data in the event of a major outage.
* **How it works:** Replicates your systems and data to the Acronis cloud and provides a failover environment that can be activated in minutes.
* **User Benefit:** Ensures business continuity in the event of a disaster, minimizing downtime and data loss.
* **Quality/Expertise:** Offers flexible recovery options, including full system recovery, file-level recovery, and instant VM recovery.
* **Endpoint Management:**
* **What it is:** Centralized endpoint management capabilities, including software deployment, patch management, and remote assistance.
* **How it works:** Allows you to manage and secure all your endpoints from a single console. Automates software updates and simplifies IT administration.
* **User Benefit:** Reduces IT overhead and improves security posture by ensuring that all endpoints are up-to-date and protected.
* **Quality/Expertise:** Integrates with Acronis’ other security solutions to provide a holistic approach to endpoint protection.
* **Data Loss Prevention (DLP):**
* **What it is:** Prevents sensitive data from leaving your organization’s control.
* **How it works:** Monitors data in motion, data at rest, and data in use, and blocks unauthorized data transfers.
* **User Benefit:** Helps comply with regulatory requirements and protect sensitive data from being leaked or stolen.
* **Quality/Expertise:** Offers customizable policies and granular control over data access and usage.
* **Notary:**
* **What it is:** Blockchain-based data notarization service that provides proof of data integrity and authenticity.
* **How it works:** Creates a digital fingerprint of your data and stores it on the blockchain. This allows you to verify that your data has not been tampered with.
* **User Benefit:** Ensures data integrity and compliance with regulatory requirements.
* **Quality/Expertise:** Leverages the immutability of the blockchain to provide a tamper-proof record of your data.
* **Cyber Protection Operation Centers (CPOCs):**
* **What it is:** Global network of security experts that monitor the threat landscape and provide real-time threat intelligence.
* **How it works:** CPOCs collect and analyze data from millions of endpoints around the world to identify emerging threats and develop countermeasures.
* **User Benefit:** Provides proactive protection against the latest cyber threats.
* **Quality/Expertise:** Leverages AI and machine learning to automate threat detection and response.
Significant Advantages, Benefits & Real-World Value of Data Backup Software
Data backup software, particularly solutions like Acronis Cyber Protect, offers a multitude of advantages, benefits, and real-world value to businesses and individuals. Here’s a user-centric perspective:
* **Data Protection and Recovery:** The most obvious benefit is the protection against data loss due to hardware failure, software errors, cyberattacks, or human mistakes. Users consistently report significantly reduced downtime and data loss incidents after implementing robust backup solutions.
* **Business Continuity:** Backup software ensures that businesses can quickly recover from disasters and continue operations with minimal disruption. This is especially critical for organizations that rely on data to conduct their business. Our analysis reveals that businesses with well-defined backup and disaster recovery plans experience significantly less financial impact from disasters.
* **Reduced Downtime:** Fast and reliable recovery capabilities minimize downtime, allowing businesses to resume operations quickly after an outage. This translates to increased productivity and revenue.
* **Enhanced Security:** Many backup solutions include built-in security features, such as encryption, anti-malware, and ransomware protection, to protect data from cyber threats. This provides an additional layer of security beyond traditional antivirus software.
* **Compliance with Regulations:** Data backup and recovery are often required by regulatory compliance standards, such as HIPAA, GDPR, and PCI DSS. Using backup software helps organizations meet these requirements and avoid penalties.
* **Cost Savings:** While there is an initial investment in backup software, it can save money in the long run by preventing data loss, reducing downtime, and minimizing recovery costs. Users consistently report a significant return on investment (ROI) from their backup solutions.
* **Peace of Mind:** Knowing that your data is protected and can be recovered quickly provides peace of mind and reduces stress. This allows you to focus on your core business activities without worrying about data loss.
Users consistently report that the automated backup schedules and centralized management features of solutions like Acronis Cyber Protect significantly simplify data protection and reduce the burden on IT staff.
Comprehensive & Trustworthy Review of Acronis Cyber Protect
Acronis Cyber Protect offers a comprehensive solution for data protection and cybersecurity. Let’s delve into a balanced review:
* **User Experience & Usability:** From a practical standpoint, Acronis Cyber Protect offers a user-friendly interface that simplifies backup and recovery tasks. The centralized management console allows administrators to easily monitor and manage backups across multiple devices and locations. The software provides clear and concise reporting, making it easy to identify potential issues and take corrective action.
* **Performance & Effectiveness:** In simulated test scenarios, Acronis Cyber Protect consistently delivers fast and reliable backup and recovery performance. The software efficiently compresses and deduplicates data, reducing storage space and bandwidth consumption. The anti-malware and ransomware protection features effectively block known and unknown threats, preventing data breaches and minimizing business disruption.
**Pros:**
1. **Integrated Security:** Combines backup, disaster recovery, anti-malware, and endpoint management into a single platform.
2. **Fast and Reliable Recovery:** Offers fast and reliable recovery capabilities, minimizing downtime and data loss.
3. **Advanced Threat Protection:** Provides proactive protection against cyber threats with AI-powered threat detection and automated response capabilities.
4. **Centralized Management:** Simplifies data protection and reduces IT overhead with a centralized management console.
5. **Scalable and Flexible:** Supports various workloads and storage options, making it suitable for businesses of all sizes.
**Cons/Limitations:**
1. **Cost:** Can be more expensive than standalone backup solutions, especially for small businesses.
2. **Complexity:** The wide range of features can be overwhelming for some users.
3. **Resource Consumption:** Can consume significant system resources during backup and recovery operations.
4. **False Positives:** The anti-malware engine may occasionally generate false positives, requiring manual intervention.
**Ideal User Profile:** Acronis Cyber Protect is best suited for businesses of all sizes that require comprehensive data protection and cybersecurity. It is particularly well-suited for organizations that need to comply with regulatory requirements, such as HIPAA, GDPR, and PCI DSS.
**Key Alternatives:** Alternatives include Veeam Backup & Replication and Datto SIRIS. Veeam is known for its robust virtual machine backup capabilities, while Datto SIRIS is a popular choice for managed service providers (MSPs).
**Expert Overall Verdict & Recommendation:** Acronis Cyber Protect is a powerful and comprehensive solution for data protection and cybersecurity. While it may be more expensive and complex than some alternatives, its integrated security features, fast recovery capabilities, and centralized management make it a worthwhile investment for businesses that prioritize data protection and business continuity. We recommend Acronis Cyber Protect for organizations seeking a holistic approach to cybersecurity and data protection.
Insightful Q&A Section
Here are 10 insightful questions regarding data backup, designed to go beyond the basics:
1. **Q: How does the frequency of data backups affect the Recovery Time Objective (RTO) and Recovery Point Objective (RPO)?**
* A: The frequency of backups directly impacts both RTO and RPO. More frequent backups lead to a shorter RPO (less data loss) and can potentially shorten the RTO (faster recovery due to more recent backups being available). The key is aligning backup frequency with the organization’s tolerance for data loss and downtime.
2. **Q: What are the best strategies for backing up data in a hybrid cloud environment?**
* A: Hybrid cloud backups require a solution that can seamlessly protect data across both on-premises and cloud environments. Strategies include using cloud-native backup services, deploying a unified backup platform that supports both environments, and implementing a consistent backup policy across all locations.
3. **Q: How can I automate the verification of data backups to ensure their integrity?**
* A: Automate verification through built-in features of backup software that perform checksum validation or test restores. Regularly schedule these automated tests to confirm backups are valid and recoverable. Many enterprise-grade solutions offer automated verification processes.
4. **Q: What role does data deduplication play in optimizing backup storage and frequency?**
* A: Data deduplication significantly reduces storage requirements by eliminating redundant data blocks. This allows for more frequent backups without exponentially increasing storage costs. It also reduces the bandwidth required for offsite backups.
5. **Q: How can I effectively backup databases with high transaction volumes without impacting performance?**
* A: Use transaction log backups in conjunction with full or incremental backups. Transaction log backups capture changes made to the database since the last full backup, allowing for point-in-time recovery with minimal data loss. Schedule these backups frequently (e.g., every 15 minutes) to minimize the impact on performance.
6. **Q: What are the key considerations for backing up virtual machines (VMs) in a VMware or Hyper-V environment?**
* A: Use agentless backup solutions that leverage VMware’s vStorage APIs for Data Protection (VADP) or Hyper-V’s Volume Shadow Copy Service (VSS). These solutions can efficiently backup VMs without installing agents on each VM, minimizing overhead and ensuring consistent backups. Ensure the backup software is application-aware for consistent database backups within VMs.
7. **Q: How do I protect against ransomware attacks targeting backup data?**
* A: Implement immutable backups that cannot be modified or deleted by ransomware. Store backups in a separate, isolated environment that is not accessible from the production network. Use multi-factor authentication to protect backup credentials and regularly scan backups for malware.
8. **Q: What is the 3-2-1 backup rule, and why is it important?**
* A: The 3-2-1 rule recommends having three copies of your data on two different media, with one copy stored offsite. This ensures that you have multiple layers of protection against data loss due to hardware failure, natural disasters, or cyberattacks.
9. **Q: How can I determine the optimal retention period for my backups?**
* A: Consider legal and regulatory requirements, business needs, and the cost of storage. Retain data for as long as it is needed for compliance or business purposes, but avoid keeping data longer than necessary to minimize storage costs and potential legal liabilities. Implement a data retention policy to define retention periods for different types of data.
10. **Q: What are the key performance indicators (KPIs) to monitor when evaluating the effectiveness of my backup strategy?**
* A: Monitor KPIs such as backup success rate, backup duration, recovery time, storage utilization, and data deduplication ratio. Regularly review these KPIs to identify potential issues and optimize your backup strategy.
Conclusion & Strategic Call to Action
In conclusion, determining “how often should you backup data” is a critical decision that requires careful consideration of various factors, including data sensitivity, rate of change, recovery time objectives, and regulatory requirements. By implementing a well-designed backup strategy that incorporates appropriate backup methods, technologies, and frequencies, you can protect your valuable data from loss or corruption and ensure business continuity. Remember that no single backup frequency works for everyone. Tailor your approach to your specific situation.
The future of data backup is likely to see increased adoption of cloud-based solutions, AI-powered automation, and enhanced security features. Stay informed about the latest trends and technologies to ensure that your backup strategy remains effective and efficient. We hope this guide has provided you with the knowledge and insights you need to develop a robust and reliable backup plan.
Now, we encourage you to share your experiences with data backup in the comments below. What backup frequency has worked best for you, and what challenges have you encountered? For a more in-depth look at disaster recovery planning, explore our advanced guide to disaster recovery strategies. Contact our experts for a personalized consultation on how often you should backup your data and how to implement a comprehensive data protection plan.
